Root Account Activity Monitor
The diagram below describes the solution at a high level.
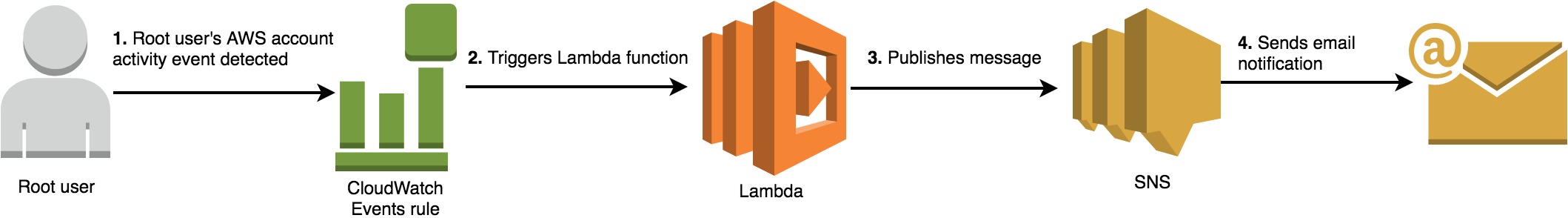
An Amazon CloudWatch Events rule detects any AWS account root user API events.
It triggers an AWS Lambda function.
The Lambda function then processes the root API event. It also publishes a message to an Amazon SNS topic, where the subject contains the AWS account ID or AWS account alias where the root API call was detected and the type of API activity.
The SNS topic then sends notifications to its email subscribers about this event.
I walk through deploying the AWS CloudFormation stack that creates these resources and then validates that root user activity is detected and notified. It helps if you know about CloudWatch Events rules, Lambda, and SNS.
Prerequisites
Create and enable a multi-region AWS CloudTrail trail for all AWS regions.
Upload the RootActivityLambda.zip file to an S3 bucket.
Deployment steps
In the CloudFormation console, choose Create Stack. Use the RootAPIMonitor.json CloudFormation JSON template. Choose Next.
Create the stack in the region in which to monitor root API activity, as well as the us-east-1 region. Root API login is a global event and logged in us-east-1. I recommend deploying in all AWS regions.
Enter the following parameter details and choose Next:
SNSTopicName: A unique name for the SNS topic to be created.
SNSSubscriptions: An email address to subscribe to the SNS topic. . I recommend sending these notifications to a distribution list rather than an individual.
LambdaTimeout: The Lambda function timeout value in seconds. The default is 30 seconds.
LambdaS3Bucket: Name of the S3 bucket where the Lambda function zip file is stored.
LambdaS3Key: Name of the Lambda function zip file. This is the full path to the S3 object, with the prefix. For example, “/dir1/dir2/lambdafunction.zip”.
Select Capabilities Acknowledgement and choose Create. This field gives permission to the stack to create IAM roles and policies. These roles and policies are used by the Lambda function to perform certain actions such as publishing messages to the SNS topic, listing the account alias, and so on.
After the CloudFormation stack completes, check for an SNS subscription email sent to the email provided for SNSSubscriptions. Open the SubscribeURL link to complete the subscription.
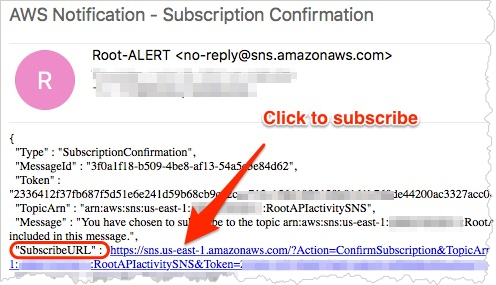
After the SNS topic is subscribed, the subscriber starts receiving email notification when root API activity is detected.
The CloudFormation template created three main AWS resources for this solution:
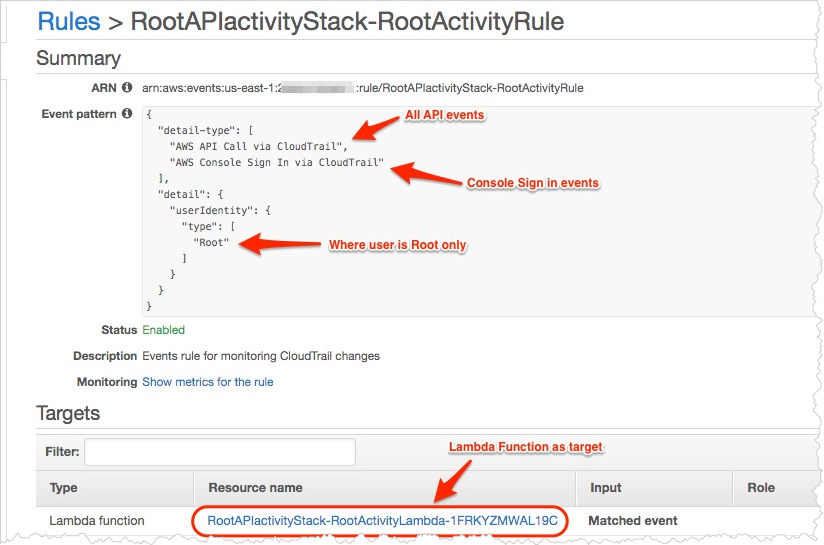
CloudWatch Events rule
The rule catches a console login event and all other API events by a root user, and triggers the Lambda function (set as a target) when such events are detected.
Lambda function
The function collects the necessary information about the root API event and publishes it to the SNS topic. The function parses the name of the event and the AWS account alias where this root API event occurred and puts them in the subject field for the message that it publishes to the SNS topic.
Code for getting the name of the event:
Code for getting the AWS account alias:
Code for publishing to the SNS topic:
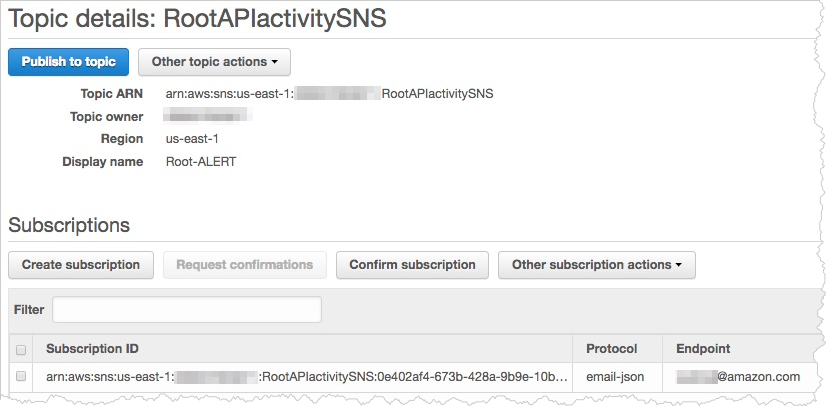
SNS topic
The topic sends the email notification published by the Lambda function.
Solution validation
Now that you have the solution deployed and ready, test and validate. First, sign in to your AWS account using your access credentials. This console login activity by a root user should send an email notification in near real time.
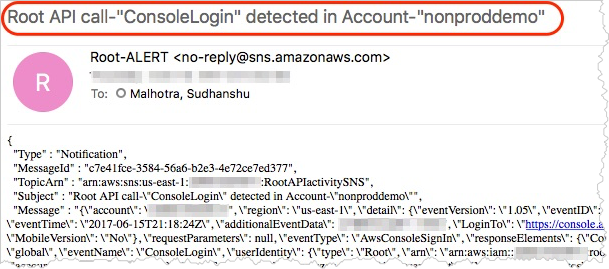
Next, validate if other root API events are also detected and notified on. For example, you can create an EBS volume using the root credentials and confirm that you receive an email notification in near real time.
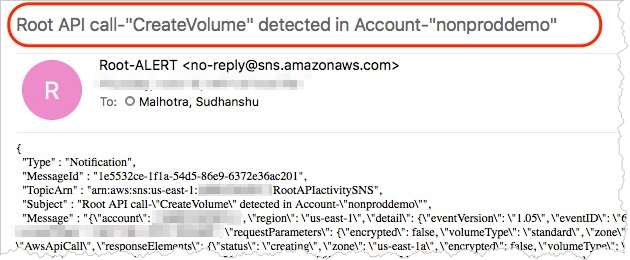
Some AWS services—such as Auto Scaling, Elastic Load Balancing, and Trusted Advisor—use root to access resources in your AWS account, instead of an IAM role. When this happens, you see the service name in the invokedBy field of the userIdentity JSON statement. This event is legitimate and can be ignored. For more information, see My AWS CloudTrail logs show root credentials are being used to authenticate actions I didn’t initiate.
Last updated